IAAA: Access Management Explained
4 security controls to secure any system
👋 Hi, this is Akash with this week’s newsletter. I write about security engineering to help you get into the world's best security teams. Thank you for your readership.
This week I’m sharing how you can secure any system with 4 control frameworks; Identification, Authentication, Authorization & Audit. Hope it’s helpful; enjoy!
Think about the last security problem you were solving.
What were you trying to do?
🤔💡 Let me take a guess.
Were you trying to protect “an asset” from “unauthorized access” to preserve the “confidentiality, integrity or availability” of the information system?
From penetration testing to encryption, everything we do in security is just that.
That’s the beauty of security.
There are thousands of controls in the market, but at the end of the day all goes back to first principles.
One of the fundamental security control frameworks is Access Management. Your ability to design a secure system relies on your understanding of,
👤 Identification
🔑 Authentication
🚦 Authorization
📝 Audit (or Accountability)
All security controls can be categorized as one of these 4 categories.
Defenders are trying to solidify them, attackers are trying to break them.
In this post, we’ll explore everything you need to know about these concepts. You’ll learn how to approach an open-ended security question the next time you see it.
📖 The Concept
We can’t build a house without a solid foundation. Let’s deep dive into the key concepts.
👤🆔 Identification
It’s about answering “Who are you?”.
Much like the physical world, you are assigned multiple identities online. The username that you enter logging into your laptop or an application. That’s your identity.
One thing to remember about identity is, most of the time identity is established “out of band” in a separate registration workflow. The first time you signed up for Substack, you probably entered an email address. For Substack, that’s your identity.
🔑✅ Authentication
It’s about proving who you say you’re.
An identity doesn’t have any inherent security control. You can claim to be anyone you want to be.
Fun fact: E-mail started off as a program that didn’t have authentication in its design.
But in the modern world, I can’t claim to be you. Well, I shouldn’t be able to.
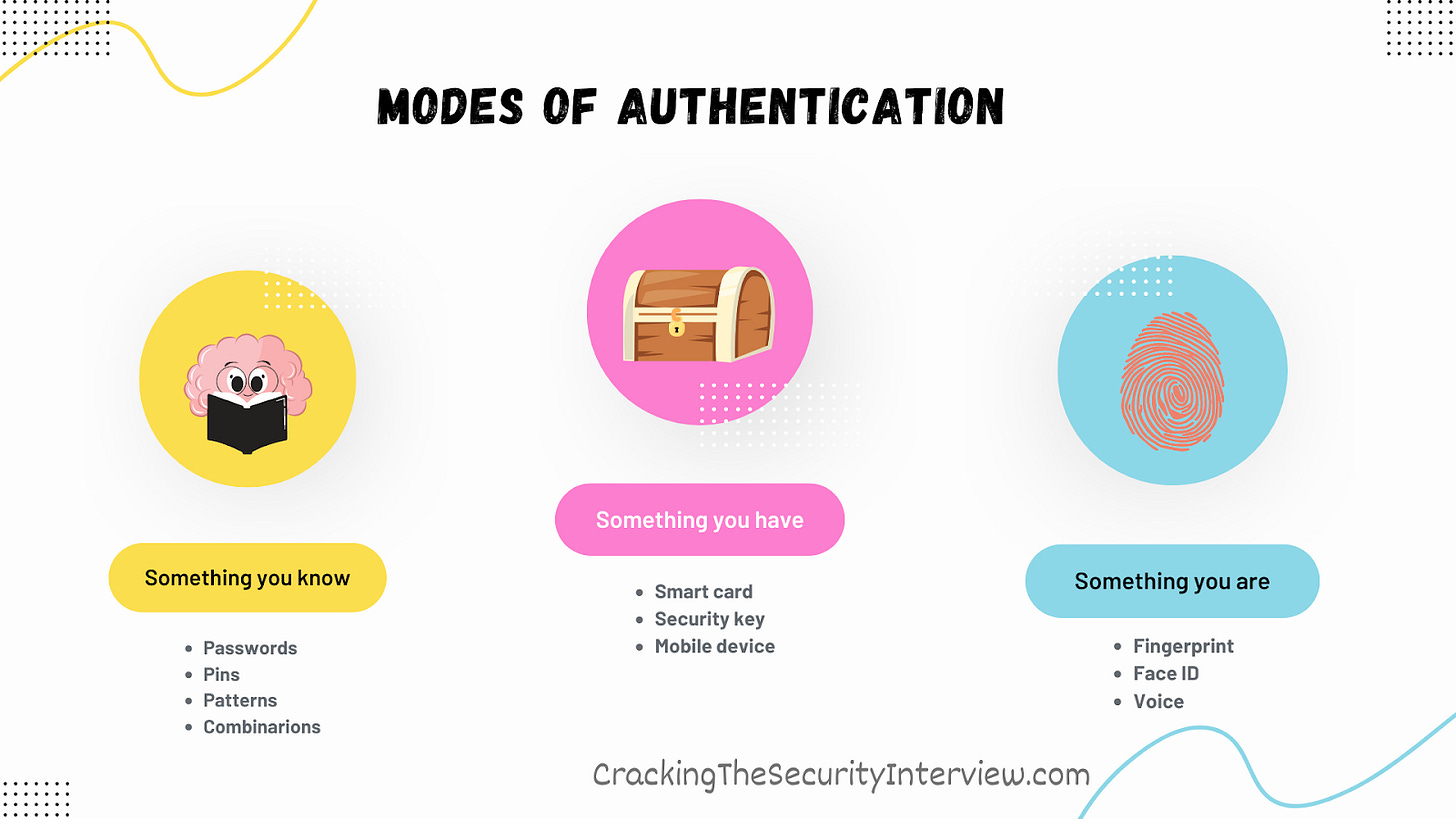
Authentication verifies your identity using one of these 3 ways:
Something you know: passwords, pins, patterns etc.
Something you have: a mobile, security key etc.
Something you are: biometrics, signature etc.
Usernames (identity) and passwords (something you know) are the most widely used authentication mechanism out there. Despite being the weakest, but that’s for some other time.
Similar to identity, authentication mechanisms also require an “out of band” registration. When you require multiple factors to authenticate, that’s called Multi-Factor Authentication (MFA). Innovative, right?
Side note: To continue reading these posts, please enable MFA across all your accounts.
🚦👮 Authorization
It’s about what you’re allowed to do after you authenticate.
Just because you are authenticated, doesn’t mean you can access everything.
Authorization controls can be thought of as a middleware that allows/denies your access request. These decisions are made based on a predetermined policy.
Fundamentally, there are two ways systems authorize you:
Access Control List: a rule-based list attached to an object, specifying which subjects (users or processes) can access it and what operations they can perform. Examples include RBAC, ABAC, file system permissions etc.
Capability List: a user or process-centric list that specifies what objects the user/process can access and what actions they can take on those objects. Session tokens, keys are examples of this.
The difference is simple, together they form the “Access Matrix”.
🔍📝 Audit
It’s about keeping a record of “Who did what, and when?”.
Audit is not a preventative security control by design. But, it’s the most useful after an incident occurs. It gives us the ability to trace “an action” back to “a subject”.
One thing to remember about audit, if it’s not immutable, there’s very little value. Logs become the attacker's first target to erase their tracks. It helps them persist on your machines longer.
Pay extra attention when designing audit logging for your systems.
🌎 Real-World Walkthrough
Let’s solidify our understanding by walking through an example.
We will use the “Substack” application to understand today’s concepts.
⚠️ Assumption: You’ve an account on Substack, please create one, if you don’t 😅.
Step 1: You clicked a link and now you’re here on this post. Do you see the “Sign In” button at the top corner?
Let’s click that and see this on the next screen:
Step 2: The “Email” it asks you to enter is the question: “Who are you?”; Identification.
Step 3: Check your mailbox, you should see an email with a signed link:
The link that you see on this email is an authenticated link. Clicking it will log you in. It’s basically something you have, access to that mailbox. Authentication.
Step 4: Now you’re logged in, let’s see what you can do. Here’s an idea, do you see this on the top right corner?
Let’s see if that “brown button” works for you. Go ahead, click it and follow through the prompts.
Oh wow, it worked! All this time, you could’ve subscribed already. I wonder what was the issue, lol.
Step 5: We certainly don’t have access to Substack logging, but check your browser history. It’s a very weak form of logging your activity. It’s not immutable, so not reliable. But you get the idea.
🌟 🔍 Parting Thoughts
In interviews, you may get asked to assess the effectiveness of a security control. Before thinking about anything else, ask yourself “what is this control doing”. Note down what it’s supposed to do. From there you’ll be able to provide a thoughtful answer. Most interviewers are looking for how clearly you understand security.
For assessing security of a system or thinking like an attacker to break it, follow this sequence:
(Identity) Who has access to this system?
(Authentication) How can I trick the system into mistaking me for someone else?
(Authorization) If I'm in, what resources do I have access to?
(Audit) Are there controls monitoring audit logs, and if so, how can I alter them?
Now, let’s do some exercise. Imagine you get a notification from an app saying your account is being accessed from another part of the world. Tell us 3 things that could’ve gone wrong, keep them grounded in fundamentals we discussed today.
Share in the comments!
🐦🔥 Interview Questions
You’re hired to design the security system for our upcoming hacker conference application. How would you approach it?
If you’re in a situation where a user needs temporary elevated access. How would you handle this authorization request securely?
How would you approach investigating a potential security breach? What types of information should be logged?
👋 💬 Get In Touch
Want to chat? Find me on LinkedIn.
If you want me to cover a particular topic in security or have feedback, you can reach out directly on akash@chromium.org.
Hope you enjoyed this content, please 🔁 share with someone who might benefit and 🔔 subscribe. Hit that like button, your 💙 response really motivates me to keep going.